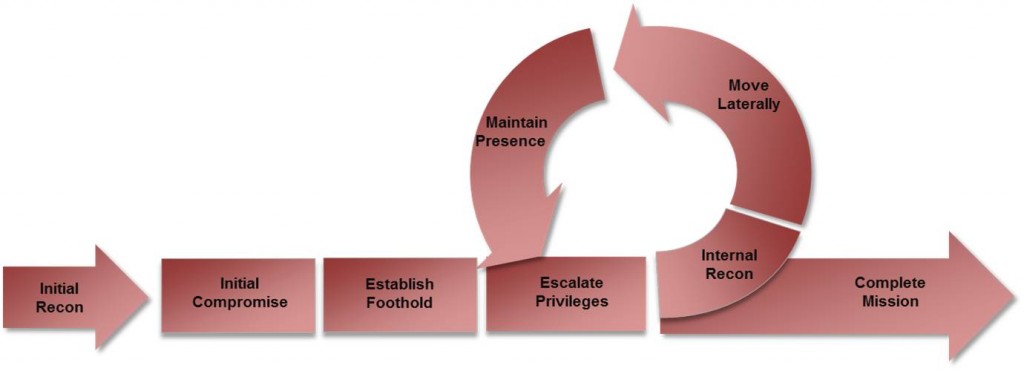
Cyber Attack Lifecycle
The process by which sophisticated cyber attacks are conducted can be described as a lifecycle. The illustration and following description has been prepared by Mandiant Consulting (a FireEye Company), a provider of incident response and information security consulting services.
Source: Mandiant Consulting, see https://www.fireeye.com/services.html.
Initial Reconnaissance: The attacker conducts research on a target. The attacker identifies targets (both systems and people) and determines his attack methodology. The attacker may look for Internet-facing services or individuals to exploit. The attacker’s research may also involve the following activities:
• Identifying websites that may be vulnerable to web application vulnerabilities
• Analyzing the target organization’s current or projected business activities
• Understanding the target organization’s internal organization and products
• Researching conferences attended by employees
• Browsing social media sites to more effectively identify and socially-engineer employees
Initial Compromise: The attacker successfully executes malicious code on one or more systems. This most likely occurs through social engineering (most often spear phishing), by exploiting a vulnerability on an Internet-facing system, or by any other means necessary.
Establish Foothold: The attacker ensures he maintains continued control over a recently compromised system. This occurs immediately following the initial compromise. Typically, the attacker establishes a foothold by installing a persistent backdoor or downloading additional utilities or malware to the victim system.
Escalate Privileges: The attacker obtains greater access to systems and data. Attackers often escalate their privileges through password hash dumping (followed by password cracking or pass-the-hash attacks); keystroke/credential logging, obtaining PKI certificates, leveraging privileges held by an application, or by exploiting a vulnerable piece of software.
Internal Reconnaissance: The attacker explores the victim’s environment to gain a better understanding of the environment, the roles and responsibilities of key individuals, and to determine where an organization stores information of interest.
Move Laterally: The attacker uses his access to move from system to system within the compromised environment. Common lateral movement methods include accessing network shares, using the Windows Task Scheduler to execute programs, using remote access tools such as PsExec, or using remote desktop clients such as Remote Desktop Protocol (RDP), DameWare, or Virtual Network Computing (VNC) to interact with target systems using a graphical user interface.
Maintain Presence: The attacker ensures continued access to the environment. Common methods of maintaining a presence include installing multiple variants of malware backdoors or by gaining access to remote access services such as the corporate Virtual Private Network (VPN).
Complete Mission: The attacker accomplishes his goal. Often this means stealing intellectual property, financial data, mergers and acquisition information, or Personally Identifiable Information (PII). Once the mission has been completed, most targeted attackers do not leave the environment, but maintain access in case a new mission is directed.
The information provided here is not intended as an endorsement of any business or individual.