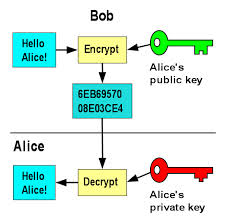
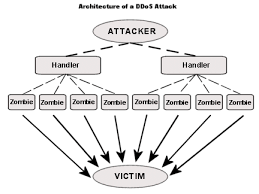
You may have heard of the terms “phishing” or even “spearphishing”—they both refer to attempts by bad actors to gain personal information to pilfer bank accounts or damage reputation. Phishing is a broader term for wide-reaching untargeted solicitations, whereas spearphishing concerns attempts to target a particular population set like veterans, the elderly, or employees of a particular company for example.
This type of targeting will be familiar with law enforcement, but what you may not know is that early hacking routines were known as “phone phreaking” and the word usage stuck.