Handling Evidence from Specific Sources
Handling Evidence from Specific Sources
- Mobile Devices
- Social media
- Internet Protocol (IP) addresses
- Internet of Things (IoT)
- Infotainment and Telematics Systems
- Peer to Peer (P2P) file sharing
Mobile Devices
For Mobile Devices that have cellular capability, the method of obtaining information will depend on the type of information being sought. For call detail records (CDRs), subscriber information, and cell site information, an investigator can send legal process to the provider. If content from the mobile device is needed, it is important to properly secure the device. The device should be disconnected from not only the cellular tower network but all radio frequencies (WiFi, Bluetooth, NFC, etc) to prevent alterations, deletions and wiping (completely erasing the device). This is done by placing the mobile device in airplane mode or placing it in a Faraday container. A faraday container can be either a bag or a box that is used to block external static and non-static electric fields by channeling electricity along and around, but not through, the container. Unless there is exigent circumstances or consent given, one can’t search through a phone without a search warrant due to Riley v. California. A trained digital forensic examiner will be needed to extract the data from the mobile device.
For best practices when encountering a mobile device please see SWGDE Best Practices for Mobile Device Forensics
Social Media
Social media changes constantly –And the dynamics of social media use can be complicated. Different social media platforms are more popular among different demographic or geographic groups. Agencies should not simply think of social media as venue to obtain evidence of a crime, but also as a tool for gathering intelligence. The intelligence can be useful for a variety of law enforcement functions, including counterterrorism, gang enforcement, policing protests, and monitoring drug trends.
The number of social media sites and apps is astounding and ever-increasing. Some of the more popular applications include: Facebook, Twitter, Instagram, Linkedin, Snapchat, Whatsapp, Kik, Investigators will need to determine a user’s username and password for most of these services to obtain more information on a specific user. This could be obtained through a simple report from a mobile device extraction to analyzing internet history to discover what platforms they are using and their potential handle.
Once you have discovered your target’s handle, you will want to serve legal process to the provider. Looking up how to serve legal process can be done by going to http://www.search.org/resources/isp-list/ and to the provider’s website. By going to the provider’s website you will also see “boiler plate” language on what is needed for specific requests and what type of legal process is needed for certain data. See below for examples.
Facebook’s U.S. Legal Process Requirements
We disclose account records solely in accordance with our terms of service and applicable law, including the federal Stored Communications Act (“SCA”), 18 U.S.C. Sections 2701-2712. Under U.S. law:
-
A valid subpoena issued in connection with an official criminal investigation is required to compel the disclosure of basic subscriber records (defined in 18 U.S.C. Section 2703(c)(2)), which may include: name, length of service, credit card information, email address(es), and a recent login/logout IP address(es), if available.
-
A court order issued under 18 U.S.C. Section 2703(d) is required to compel the disclosure of certain records or other information pertaining to the account, not including contents of communications, which may include message headers and IP addresses, in addition to the basic subscriber records identified above.
-
A search warrant issued under the procedures described in the Federal Rules of Criminal Procedure or equivalent state warrant procedures upon a showing of probable cause is required to compel the disclosure of the stored contents of any account, which may include messages, photos, videos, timeline posts, and location information.
-
We interpret the national security letter provision as applied to Facebook to require the production of only 2 categories of information: name and length of service.
Kik’s Guide for Law Enforcement
- Agencies outside of Canada may need to submit a Mutual Legal Assistance Treaty (MLAT) request through the proper legal authorities in order to obtain any user data from us.
There are several resources that can help agencies with open source intelligence (OSINT) from Facebook, Twitter, Instagram, LinkedIn, YouTube and more. A few of resources would be Intel Techniques and OSINT Framework These sites can allow you to pivot from one piece of information to the other by quickly searching/querying information about your target to directing you to other websites that can aide you in your investigation.
Internet Protocol (IP) Addresses
IP addresses are often instrumental in internet investigations. Every device that connects to the internet requires an IP address. An IP address can be provided by a company like Facebook or Twitter for a person’s recent login IP address or from a website that is capturing traffic and logging IP addresses. These IP addresses can be used to identify an Internet Service Provider (ISP) like Xfinity and with the proper legal authority, the provider can share who was leasing that IP address.
There are two versions of IP addresses, IPv4 and IPv6. IPv4 (see example below) is currently the most common; however due to a shortage of IPv4 addresses, IPv6 (see example below) was created to allow more devices to connect to the internet. An investigator may need to discover and track an IP address from a suspect’s use of the internet. This includes, but is not limited to, investigations into peer-to-peer programs, social media or email. The same school of thought with “following the money” applies with IP addresses.
Example of an IPv4 address: 50.131.23.170
Example of an IPv6 address: 2001:cdba:0000:0000:0000:0000:3257:9652, 2001:cdba:0:0:0:0:3257:9652, or 2001:cdba::3257:9652
Investigators can then subpoena the internet service provider to get subscriber information and a physical address for that account. This information should be verified through other means. A few sites that can facilitate this are http://whois.domaintools.com/ and http://centralops.net/co/ both sites will show you the registrar information of the IP address or Domain. The information provided may not be accurate.

Internet of Things (IoT)
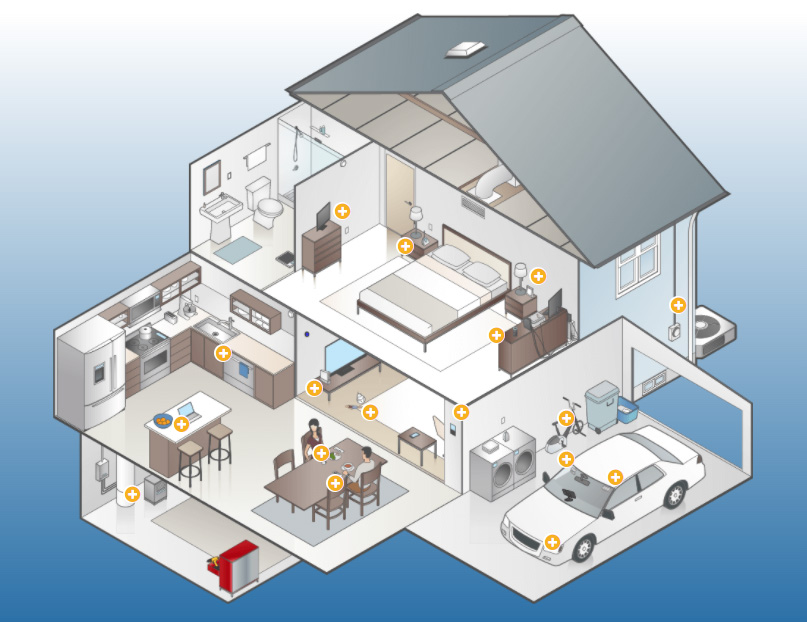
The Internet of Things (IoT) is the inter-networking of physical devices, vehicles (also referred to as “connected devices” and “smart devices”), buildings, and other items embedded with electronics, software, sensors, actuators, and network connectivity which enable these objects to collect and exchange data.
Cameras are more and more common in today’s homes for home monitoring but they can also be within a refrigerator or a doorbell. With the addition of these inside a home an investigator could find information that could be beneficial for an investigation. Looking at any IoT device could reveal patterns, activity or other data that could be the missing piece to the puzzle.
Click here for an interactive walk-through of today’s smart home.
Infotainment and Telematics Systems
Examiners should be aware that a vehicle’s digital systems are like any other digital device/system and therefore must be handled appropriately to prevent data destruction. A modern day vehicle will contain multiple computers and/or networks and therefore the examiner should take reasonable measures to isolate the vehicle from wireless networks (e.g. WiFi, cellular, Bluetooth, etc.).
Tools also exist to extract way-point data from stand-alone GPS devices (so long as these devices are powered on). One such website, Berla iVe, supports the extraction of infotainment data from vehicles. Vehicle infotainment and telematics systems store a vast amount of data such as recent destinations, favorite locations, call logs, contact lists, SMS messages, emails, pictures, videos, social media feeds, and the navigation history of everywhere the vehicle has been. Many systems record events such as when and where a vehicle’s lights are turned on, which doors are opened and closed at specific locations, and even where the vehicle is when Bluetooth devices connect. iVe currently supports many different vehicle from different manufactures to include but not limited to (Ford, Chevrolet, GMC) and is rapidly expanding its acquisition and decoding capabilities more and more vehicles. The hardware and software currently supports extracting data via logical and physical acquisitions from over 5200 different models of vehicles. It can decode data from infotainment and telematics systems and reveal quintessential data in an investigation.
For best practices when encountering a vehicle you suspect that has an Infotainment and Telematics System please see SWGDE Best Practices for Vehicle Infotainment and Telematics Systems paper.
Emails
The investigator should determine where items of evidentiary value are stored. Digital evidence, in particular data stored by other entities such as internet service providers, is often volatile and cannot be recovered. Email that goes through companies like Gmail and Yahoo and are stored on the servers of their respective companies.
For this reason, it is very important to send preservation letters out before a suspect can dispose of any evidence. Many commercial providers, such as Yahoo, change their policies often. One helpful resource is http://www.search.org/resources/isp-list, which maintains a comprehensive Internet Service Provider (ISP) list along with other online content providers. Instructions for how to obtain information, whether via subpoena, court order(s) and/or search warrants, are provided in this database along with contact information and current Law Enforcement Guides which outline the company’s information-sharing policy.
A number of websites sites can explain how to read an email header in order to abstract the sender’s IP address. For example:
- http://www.howtogeek.com/108205/htg-explains-what-can-you-find-in-an-email-header
- http://kb.mediatemple.net/questions/892/Understanding+an+email+header
- http://ipaddress.com/trace-email.html
Peer to Peer File Sharing (P2P)
Peer to peer file sharing is the sharing of digital media using networking technology. P2P sharing can be used for legitimate purposes, but it is frequently used for sharing illegal materials like pirated media and child exploitation/pornography videos. These investigations are typically conducted by regional Internet Crimes Against Children (ICAC) task forces. In order to access the training catalog one will need to be a part of an ICAC task force. If you or your agency is not a part of an ICAC task force please contact an appropriate Commander in your area by going to the link here.